The Internet Protocol Security (IPSec) Site-to-Site VPN feature allows you to establish IPSec VPN tunnels from the Virtual Office in the Axcient Cloud to any standard compliant IKEv2 IPSec VPN gateway on your local network.
Specially, you can use this feature during a site disaster to:
- Recreate the network in an organization with two or more sites linked together in a corporate network
- Temporarily replace a connection while a machine room is rebuilt after a disaster
NOTE: IPSEC Site-to-Site VPN is not recommended in a test environment.
Set up an IPSec Site-to-Site VPN connection
To set up an IPSec Site-to-Site VPN connection, you must turn on the feature in your Virtual Office and then
1. Enable port forwarding
Port forwarding is not enabled by default but can be configured to work in a virtual office.
NOTE: Enabling port forwarding could lead to network collisions if configured on a test virtual office.
- Do not enable and configure port forwarding for a test virtual office as productivity and data loss might occur.
Additionally, Port forwarding must be enabled for Site to Site Open VPN to function.
To configure or edit the port forwarding settings:
1. On the Configure: Virtual Office page, click the Edit button in the Port Forwarding section.
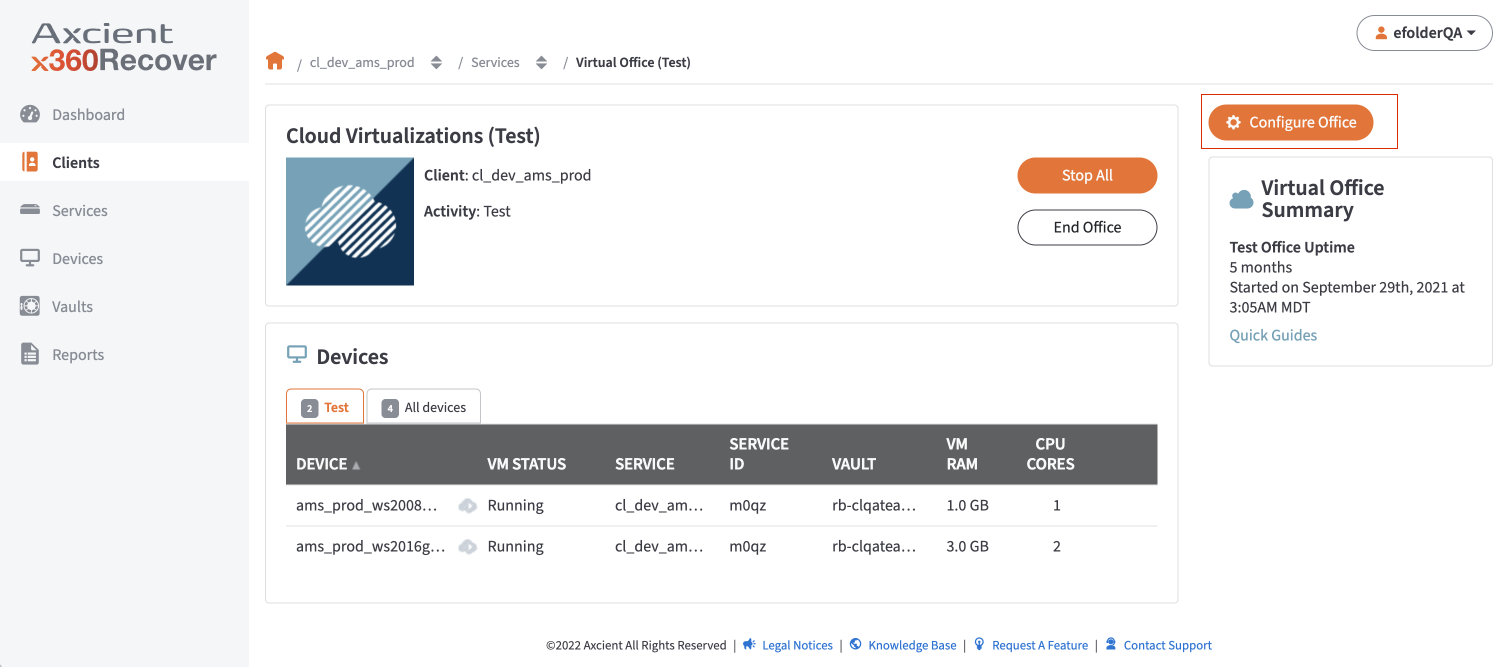
2. On the Port Forwarding screen, update the following fields:
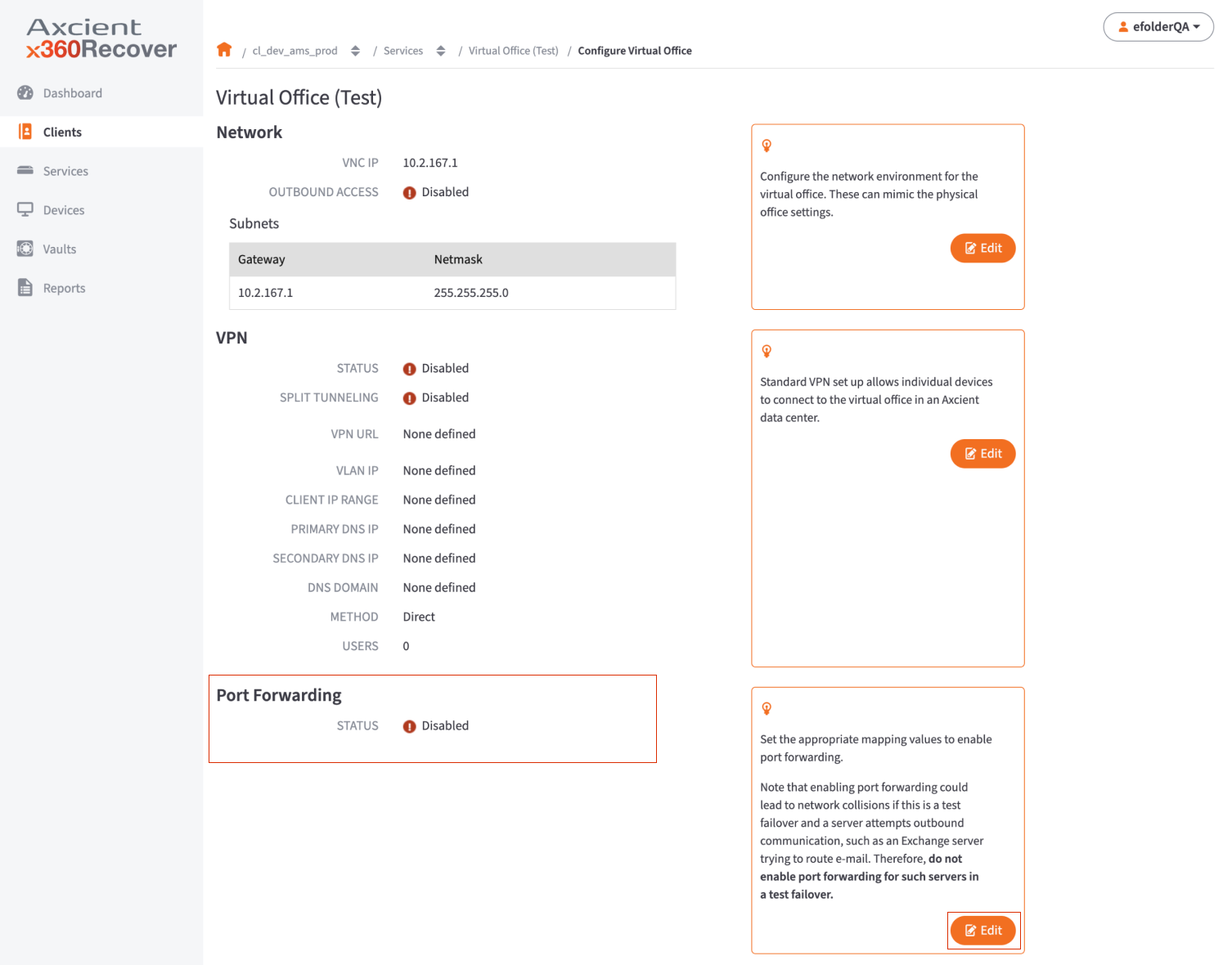
a.) Enable the Port Forwarding option.
b.) Enter the appropriate values to set the port forwarding rules:
- In the Ext Port field, enter the external port number to be forwarded.
- In the Internal IP field, enter the internal IP address. The internal IP address must fall inside one of the Virtual Office's subnets.
- In the Int Port field, enter the internal port number.
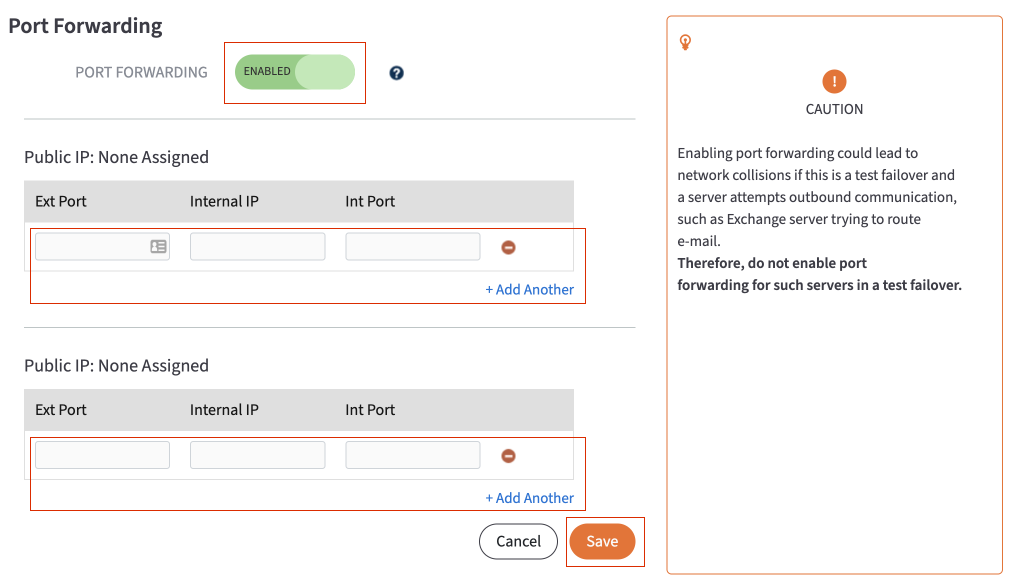
c.) Click the Add Another button to add additional entries. Repeat these steps as many times as necessary.
4. Click the Save button to save any new configurations.
2. Configure the site-to-site IPSec VPN settings
After Port Forwarding settings have been configured, navigate to the Site-to-Site IPSec VPN section and click the Edit button.
You can configure the following options:
- Click the S2S IPSec option to enable Site-to-Site IPSec VPN settings.
- In the Site Public IP field, enter the public IP address of the remote machine or hardware with IPSec software (for example, Cisco ASA).
- In the Site Local Subnets section, enter the remote subnets and associated netmasks for sharing with the Virtual Office subnets. Please note that these subnets do not need to intersect with the Virtual Office subnets.

Click Save when you are finished.
Delete3. Configure gateway settings
Gateway settings
You can connect with any standard compliant IKEv2 IPSec VPN gateway.
When configuring your router or firewall to connect to the Axcient Virtual Office IPsec VPN, use the following encryption settings
IPsec Phase 1 Settings
|
DH Group 5 or 14 Note: Settings with DH Group 14 can be only used with AES 256 bit encryption and SHA-384 hash key |
|
AES 256 bit encryption |
|
SHA-1, SHA-256 or SHA-384 can be used for the hash key |
|
Lifetime 3600 seconds |
IPsec Phase 2 Settings
|
DH Group 5 or 14 Note: Settings with DH Group 14 can be only used with AES 256 bit encryption and SHA-384 hash key |
|
AES 256 bit encryption |
|
SHA-1, SHA-256 or SHA-384 can be used for the hash key |
|
Lifetime 3600 seconds |
SUPPORT | 720-204-4500 | 800-352-0248
- Contact Axcient Support at https://partner.axcient.com/login or call 800-352-0248
- Have you tried our Support chat for quick questions?
- Free certification courses are available in the Axcient x360Portal under Training
- Subscribe to Axcient Status page for updates and scheduled maintenance
1423 | 1971